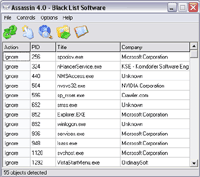
When malicious software invades your system, the most invasive ones will ensure that they are malignant. They will do this by editing the registry, installing browser helper objects, hijacking the Internet connection with layer service providers and, sometimes all of the above. Some backdoor software will spawn or create clones of themselves in order to regenerate and become quite difficult to remove. Most Spyware scanners will not be able to baptize the system until these programs shut down and your scanners are not capable of doing this when the malicious software regenerates. Even deleting their entries found in the registry may not help considering that some malware will detect this change and add themselves back into the registry. Therefore, one must reboot into Safe Mode in order to ignore the startup list; however, it is now possible to detect, suppress, and remove these malignant processes without rebooting at all. With the release of Assassin version 1.0, anyone operating a personal computer can recover a hijacked network based Windows operating system within minutes and all without rebooting or changing the system configurations.
Download